MAC Layer Attacks in Wireless Sensor Networks (a simple case)
Preface: An inexpensive jammer can be used to cause severe damage or to disrupt future generation networks. This small project evaluates a basic scenario and shows the impact of probabilistic jamming in wireless sensor networks. Our results show that a single jammer may not be effective to disrupting the network, instead, using a higher jamming probability and a combination of two or more jammers activated one after another is more efficient.
This work was developed as part of the PhD course in EP3300/ANSS - Advanced Networked Systems Security @ KTH
Introduction
Wireless jamming have been studied for many years. Particularly, there is an extensive early work focused on 802.11 networks, just to name a few [1]-[3], since these are still the most common wireless networks. However, and more recently, wireless sensor networks will dominate the wireless networks, because, of the emergence of Internet Of Things (IoT). The IoT is expected to connect every device the Internet. The emergence of Wireless Sensor Networks (WSN) have opened many opportunities in the areas of machine-to-machine (M2M)[4],[5]. The nature of wireless communications and its expected extensive deployment, makes such networks vulnerable to jamming attacks. Jamming attacks are characterized by a malicious node sending a burst of strong signal, with the sole intent of destroying legitimate traffic that transits a network [6]. The impact of such an attacks are severe:
they affect routing paths, causing network reliability to drop;
jamming also increase the energy consumption in the network, because a node not receiving any ACK from the medium access control would continuously sending a packet.
Such attacks are perhaps easier to detect on Wi-Fi networks since the location of the access points are well knows, and normally cover smaller networks. In WSN, the scale of the problem is larger. WSN are in many cases deployed into factories, wildness and streets to monitor vital information of the environment or an industrial process. Therefore, it is important to study the effects of jamming on such networks.
In recent years, much attention have been devoted to research in energy-efficient communications. Many efficient medium access control (MAC) prototypes have been proposed [7]-[11]. However, little attention was given to the issues related to the deployment and operating wireless sensor networks. With large scale deployments envisioned in the future, new challenges arise.
Goals
In this work we consider a simple example of data jamming in WSN. The adversary (illegitimate node) also runs the same MAC and routing protocol as the legitimate nodes. We depart from previous approaches, because we do not use selective jamming [6], since we consider it energy-wasteful. The need to decode and analyze packets as it done for example in [6], it is a bad idea in WSN. Because, in networks such as WSN, energy conservation is a key aspect. We, therefore, address the case where the the jammer is only interested in disrupting network activity.
Contributions
In this project we address the effects of jamming attacks on multihop wireless sensor networks. More specifically, we consider the effects of jamming on end-to-end packet latency, and on energy consumption of nodes that are part of the routing paths. To this end, we make the following contributions:
First we design, and implement a small scenario for jamming attacks in wireless sensor networks.
Secondly, we analyze and evaluate the impact of jamming attacks on the end-to-end delay, and network reliability.
Problem formulation and models
This section addresses the problem formulation and describes the models we use.
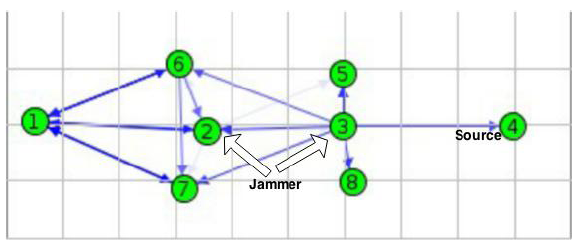 |
Figure 1: Network scenario topology under study. One data packet source node |
Problem formulation
We consider a network in Figure 1.
The sink node  and the source node
and the source node  communicate over a wireless sensor network.
Two jammer nodes are part of the same wireless network posing as legitimate
nodes. These jammers are also part of the
routing tree. To save energy, both nodes do not use any packet classification.
To hide their activities as well as to save energy, jammer nodes
use jamming probability
communicate over a wireless sensor network.
Two jammer nodes are part of the same wireless network posing as legitimate
nodes. These jammers are also part of the
routing tree. To save energy, both nodes do not use any packet classification.
To hide their activities as well as to save energy, jammer nodes
use jamming probability 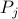 (probability of jamming) to send
a train of packets (jamming signal). We are interested in analyzing
the effect of jamming into the end to end packet delay.
In our example, the attacker does not use a special hardware,
it is made of the same hardware as the legitimate nodes.
The effectiveness of the attack comes from the fact that
the attacker have full knowledge of the implementation and
the internal workings of the communication protocols.
(probability of jamming) to send
a train of packets (jamming signal). We are interested in analyzing
the effect of jamming into the end to end packet delay.
In our example, the attacker does not use a special hardware,
it is made of the same hardware as the legitimate nodes.
The effectiveness of the attack comes from the fact that
the attacker have full knowledge of the implementation and
the internal workings of the communication protocols.
Network model
We consider a network of wireless capable nodes, that communicate over wireless. At boot up, nodes form a Collection tree to route packets to the sink. The tree is formed using an open-stack and well-known implemented version of the Collection Tree Protocol (CTP) [12]. While the routing metric is the expected transmission count (ETX) [13]. Since packets traverse many hops to reach destinations, any disruption in one of the routing nodes, causes an increase into the end to end packet delay. For simplicity, we consider that packets are not encrypted, or intruder nodes have no intention of modifying the contents of a packet. Instead, they are interested in disrupting the network.
Apart from the source node, intermediate nodes do not generate data packets. However, they generate routing information packets needed to update the network topology. Although the model we present here is very simple, we restrict ourselves to a single data traffic source. Because, it gives a good insight into the problem under study, since a more complicated model can be derived from this model. On the other hand, it is hard to analyze the effect of jamming if the packets are coming from multiple sources.
Adversary model
In our model, the adversary have a full knowledge of the
network, MAC and the routing protocols, since those protocols
are open-source [7], [12], [14], [15]. Therefore, the adversary
is also able to be part of the routing tree. To avoid detection,
the adversary does not modify any packets.
To jam packets, the adversary uses a probabilistic approach:
With probability 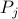 the adversaries behave as illegitimate
nodes, and consequently send a variable burst of jamming
packets. While with probability
the adversaries behave as illegitimate
nodes, and consequently send a variable burst of jamming
packets. While with probability 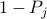 they behave as legitimate
nodes. For our evaluations, the size of the burst varies
between 30 and 35 packets, and each packet is 127 bytes (the
maximum packet size allowed in IEEE 802.15.4 networks).
they behave as legitimate
nodes. For our evaluations, the size of the burst varies
between 30 and 35 packets, and each packet is 127 bytes (the
maximum packet size allowed in IEEE 802.15.4 networks).
Impact and effectiveness of jamming attacks
Impact of jamming attacks
On packet end-to-end latency: The presence of a burst of packets on the medium (air) not addressed to any of the legitimate nodes, causes these nodes to back off and return into the inactive mode. The presence of many adversary nodes, when they jam the medium one after the other, renders the medium unusable for long periods of time. Any legitimate traffic traversing the network will suffer long queuing delays at the intermediate nodes. As a result the end-to-end latency of such traffic increases dramatically.
The jamming attacks are probabilistic, and there is no coordination amongst the attackers, it is difficult to have sequential activation of the two attackers. However, when they happen, their effect as we will show in the graphs is very noticeable.
On energy consumption: Now lets briefly change our focus on energy-consumption. Jamming attacks increase the the energy-consumption 16. Consider a simple example as a unicast packet on the transmission buffer of a legitimate node. Such a node will attempt to deliver that packet to the next hop. Now consider that a node makes a CCA and the channel is considered clear, however, when attempting to send that packet (CCA time
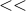 packet transmission time) it always collides.
After the maximum number of attempts per path, that node
will try to select another path to forward that packet. This
is exactly the effect of having
packet transmission time) it always collides.
After the maximum number of attempts per path, that node
will try to select another path to forward that packet. This
is exactly the effect of having 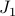 and
and 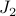 in the network. The
conclusion is that nodes that are part of the routing path whose
transmitted packets are jammed will have their energy budget
increased.
in the network. The
conclusion is that nodes that are part of the routing path whose
transmitted packets are jammed will have their energy budget
increased.
Effectiveness of Jamming Attacks
Single node jammer (ineffective): Throughout our experimental evaluation, we observed that probabilistic jamming with a single jammer is not effective. Common techniques such as CCA, transmission phase-lock are enough to smooth the effects of presence of a jammer in the network. In figure 2 it shows our network scenario in operation. The upper corner shows the network topology. The network routing tree is visible, and node 4 routes its packets through nodes 8, 7 and finally 1. The upper center display shows the network output for debugging purposes only.’ The lower display it shows the timeline.
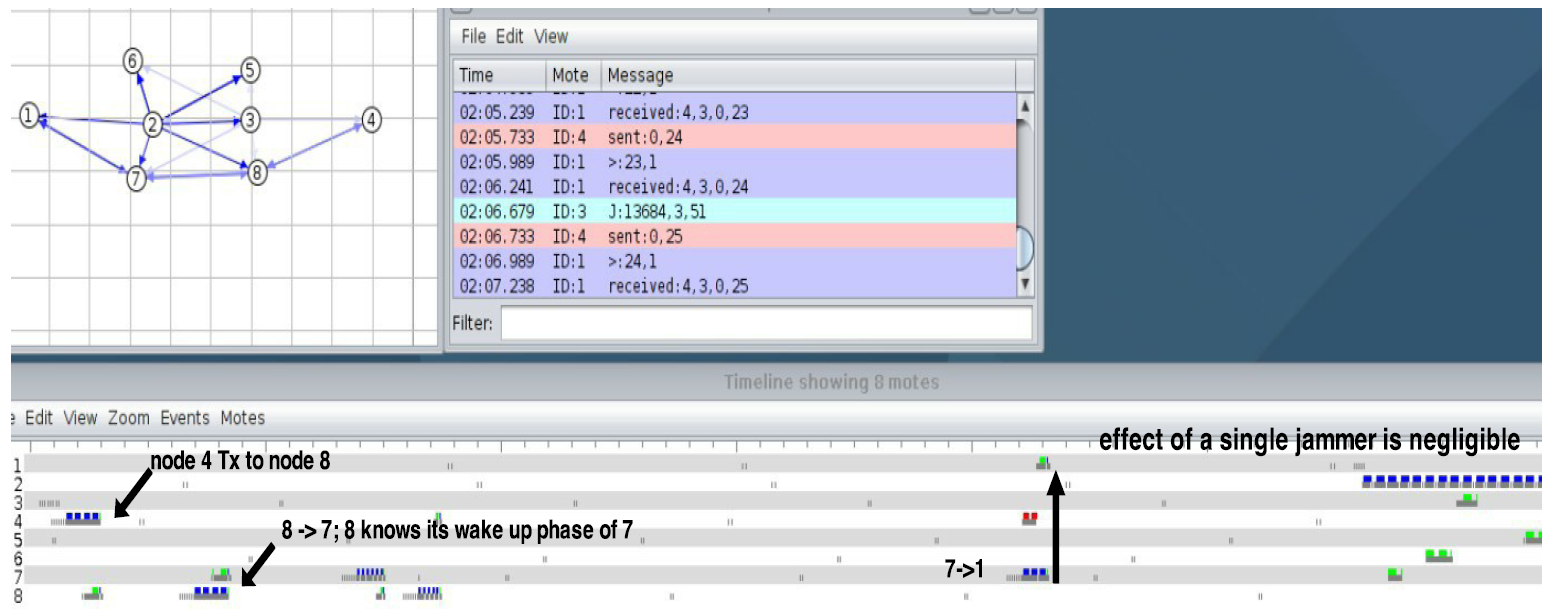 |
Figure 2: The timeline shows the actual network operation with active and inactive periods shown (radio ON/OFF). It also displays the clear channel assessment (CCA appears as a short radio activation). The blue rectangles are packet transmissions, while the green rectangles are packet receptions. The red rectangles are collisions or interfered packets. |
Observation: An example of ineffective jamming attack. Node 4 (source) initiates a communication to node 1. It delivers a packet to node 8, which has previously recorded the transmission phase of node 7. Once the packet is at node 7, it delivers it successfully to node 1. When the jammer node enters into activity, it is effect on the data packet is negligible.
Two or more jammer nodes (effective): In this case, we illustrate the case where jamming completely disrupts all traffic in the network. The two jammer nodes activate one after another bringing all network traffic to halt. In the figure 3 after node 2 has finished jamming node 4 attempts to transmit a packet using the last known best path (
 ). However, node
5 have no valid path to forward the packet, and it returns it
to node 4. Node 4 detects a routing loop, and tries fast path
discovery. Another jammer node (node 2) enters into activity
which causes node 4 to waste energy before giving up. This
case captures effective jamming, because not only data traffic
but routing paths become inconsistent due to jamming.
). However, node
5 have no valid path to forward the packet, and it returns it
to node 4. Node 4 detects a routing loop, and tries fast path
discovery. Another jammer node (node 2) enters into activity
which causes node 4 to waste energy before giving up. This
case captures effective jamming, because not only data traffic
but routing paths become inconsistent due to jamming.
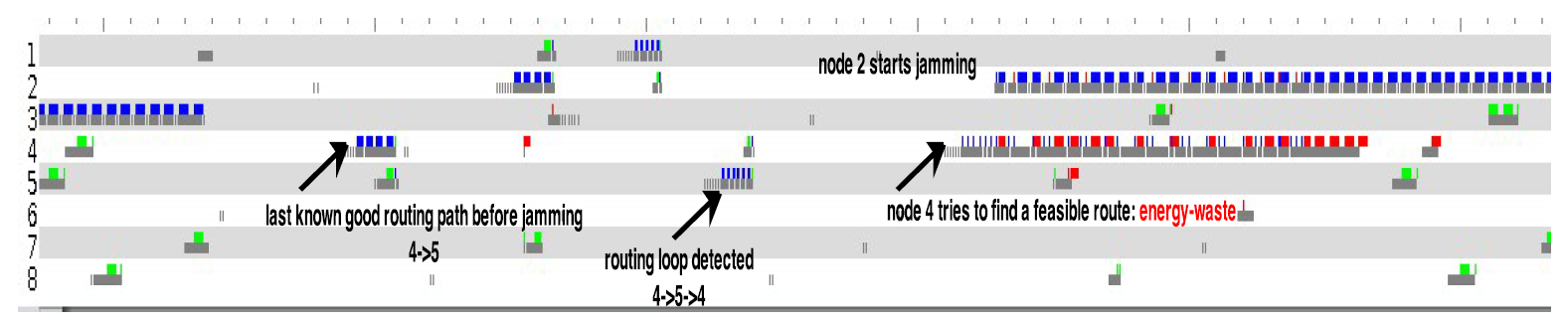 |
Observation: An example of effective jamming attack. After node 2 has finished jamming node 4 attempts to transmit a packet using the last known best path
( ). However, node 5 have no valid path to forward the packet, and it returns it to node 4. Node 4 detects a routing loop, and tries fast path discovery.
Another jammer node (node 2) enters into activity which causes node 4 to waste energy before giving up.
). However, node 5 have no valid path to forward the packet, and it returns it to node 4. Node 4 detects a routing loop, and tries fast path discovery.
Another jammer node (node 2) enters into activity which causes node 4 to waste energy before giving up.
Results
Evaluation scenario desription
In Figure 1 node 4 has a data rate of one packet a second. Intermediate nodes do not generate any data traffic, only routing related traffic. At the destination (node 1) we record the average throughout, the packet end-to-end latency. Depending on the activity of the intermediate nodes, we are able to analyze the network in real time. Each jammer contains a task that is activated probabilistically. We vary the jamming probability from 0 (no jamming) to 0.7 (total disruption). However, since all jammers are battery powered, using a larger jamming probability would increase their energy consumption, limiting the duration of the attacks to some hours.
Network throughput
We measure the network throughput in snapshots of 10 seconds. This way we were able to capture instants of time when the jammers disrupt the network. In Figure 4 we show such network output using different jamming probabilities. The x − axis is the elapsed time, while the y − axis is the network through in a snapshot of 10 seconds.
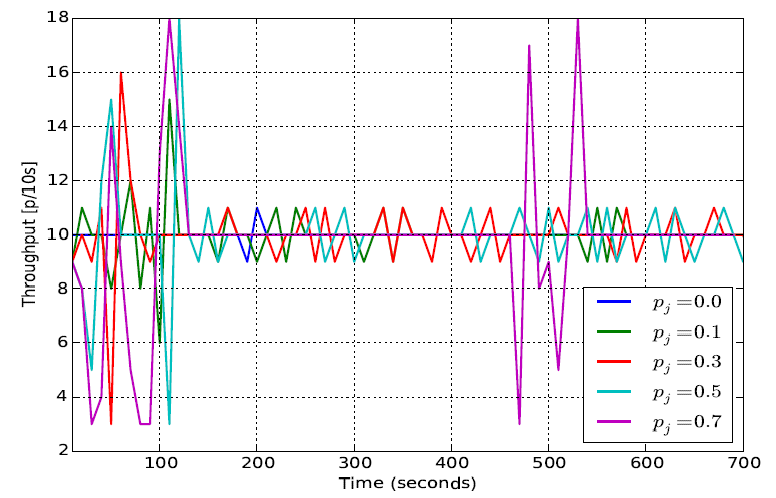 |
Figure 4. We measure the network throughput in snapshots of 10 seconds. |
Packet end-to-end latency
This result is very important for network design, since it provides insights of the expected packet end-to-end latencies. A designer of control applications over wireless, could for example use these results to set an optimal sampling period when the network is under attack (see for example Figure 6). In Figure 5 each packet contains a time-stamp which records the time it was generated, and the time it was received at the destination. This information allowed us to compute the end to end latency for each packet. Because, intermediate nodes were configured to not discard packets.
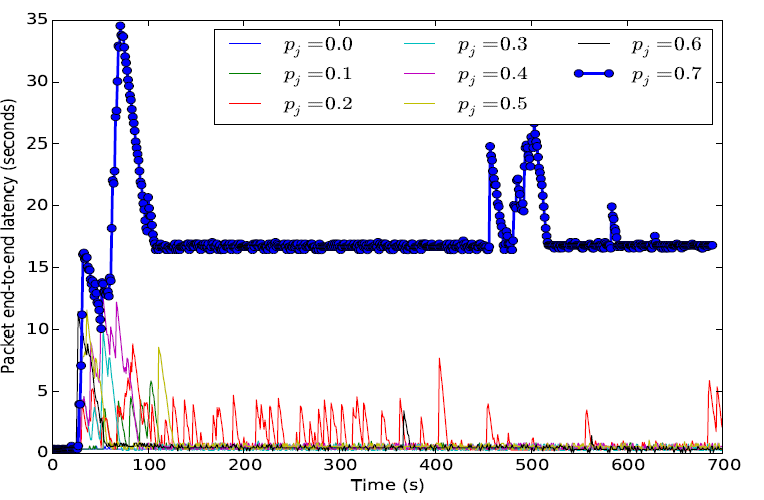 |
Figure 5. End-to-end latency due to jamming attacks |
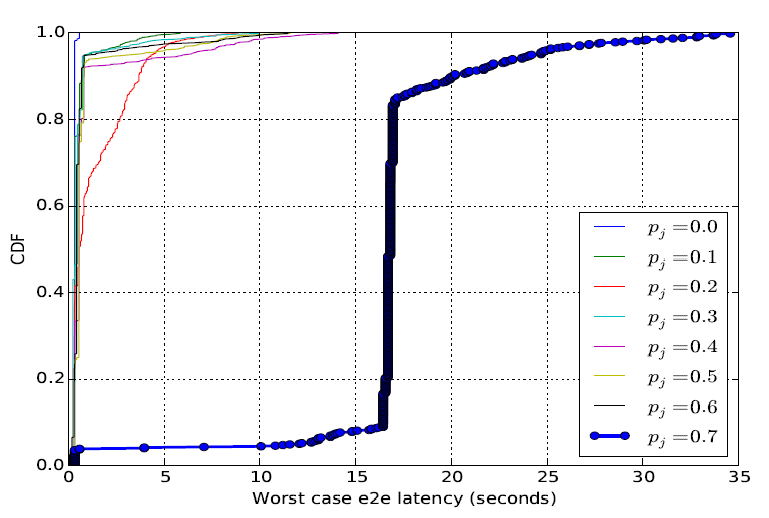 |
Figure 6. CDF of the end-to-end latency due to jamming attacks |
Observation: This result is very important for network design, since it provides insights of the expected packet end-to-end latencies. A designer of control applications over wireless, could for example use these results to set an optimal sampling period when the network is under attack (see for example Figure 6).
Conclusion and final remarks
This report demonstrated the feasibility of jamming a wireless
network with the sole intent of disrupting the network.
Two jammer nodes were used to impersonate as legitimate
nodes. These jammers played two roles, as legitimate nodes
as well as as jammers. Their behavior changes according to
probability 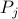 ; the jamming probability. Our results show that
when two jammers become active one after the other finishes
jamming the medium, their combined effect is very disruptive
to the network. They cause the packet end-to-end latency
to increase significantly. Future directions, would include the
addition of coordination amongst jammers.
; the jamming probability. Our results show that
when two jammers become active one after the other finishes
jamming the medium, their combined effect is very disruptive
to the network. They cause the packet end-to-end latency
to increase significantly. Future directions, would include the
addition of coordination amongst jammers.
Final remarks
The results demonstrated the main weakness of single channel MAC layer protocol. They give a compeling case, why channel hopping is more resilient against only to fight interference and channel fading, but it is also an effective measure against jamming attacks.
Observation: a channel-hopping MAC layer protocol, increases the cost for a jamming attack to succeed.
References
[1] W. Xu, W. Trappe, Y. Zhang, and T. Wood, “The feasibility of launching and detecting jamming attacks in wireless networks,” in Proceedings of the 6th ACM international symposium on Mobile ad hoc networking and computing. ACM, 2005, pp. 46–57.
[2] V. Navda, A. Bohra, S. Ganguly, and D. Rubenstein, “Using channel hopping to increase 802.11 resilience to jamming attacks,” in INFOCOM 2007. 26th IEEE International Conference on Computer Communications. IEEE. IEEE, 2007, pp. 2526–2530.
[3] E. Bayraktaroglu, C. King, X. Liu, G. Noubir, R. Rajaraman, and B. Thapa, “Performance of ieee 802.11 under jamming,” Mobile Networks and Applications, vol. 18, no. 5, pp. 678–696, 2013.
[4] A. Bartoli, M. Dohler, J. Hern´andez-Serrano, A. Kountouris, and D. Barthel, “Low-power low-rate goes long-range: the case for secure and cooperative machine-to-machine communications,” in NETWORKING 2011 Workshops. Springer, 2011, pp. 219–230.
[5] J. Gubbi, R. Buyya, S. Marusic, and M. Palaniswami, “Internet of things (iot): A vision, architectural elements, and future directions,” Future Generation Computer Systems, vol. 29, no. 7, pp. 1645–1660, 2013.
[6] A. Proano and L. Lazos, “Selective jamming attacks in wireless networks,” in Communications (ICC), 2010 IEEE International Conference on. IEEE, 2010, pp. 1–6.
[7] M. Buettner, G. V. Yee, E. Anderson, and R. Han, “X-mac: a short preamble mac protocol for duty-cycled wireless sensor networks,” in Proceedings of the 4th international conference on Embedded networked sensor systems. ACM, 2006, pp. 307–320.
[8] O. D. Incel, L. van Hoesel, P. Jansen, and P. Havinga, “MC-LMAC: A multi-channel MAC protocol for wireless sensor networks,” Ad Hoc Networks, vol. 9, no. 1, pp. 73–94, 2011.
[9] I. Rhee, A. Warrier, M. Aia, J. Min, and M. L. Sichitiu, “Z-mac: a hybrid mac for wireless sensor networks,” IEEE/ACM Transactions on Networking (TON), vol. 16, no. 3, pp. 511–524, 2008.
[10] A. El-Hoiydi and J.-D. Decotignie, “Wisemac: An ultra low power mac protocol for multi-hop wireless sensor networks,” in Algorithmic Aspects of Wireless Sensor Networks. Springer, 2004, pp. 18–31.
[11] G. Lu, B. Krishnamachari, and C. S. Raghavendra, “An adaptive energyefficient and low-latency mac for data gathering in wireless sensor networks,” in Parallel and Distributed Processing Symposium, 2004. Proceedings. 18th International. IEEE, 2004, p. 224.
[12] O. Gnawali, R. Fonseca, K. Jamieson, D. Moss, and P. Levis, “Collection tree protocol.”
[13] D. S. De Couto, “High-throughput routing for multi-hop wireless networks,” Ph.D. dissertation, Massachusetts Institute of Technology, 2004.
[14] A. Dunkels, B. Gronvall, and T. Voigt, “Contiki-a lightweight and flexible operating system for tiny networked sensors,” pp. 455–462, 2004.
[15] A. Dunkels, “The contikimac radio duty cycling protocol,” 2011.
[16] K. Pelechrinis, M. Iliofotou, and S. V. Krishnamurthy, “Denial of service attacks in wireless networks: The case of jammers,” Communications Surveys & Tutorials, IEEE, vol. 13, no. 2, pp. 245–257, 2011.
[17] F. Osterlind, A. Dunkels, J. Eriksson, N. Finne, and T. Voigt, “Crosslevel sensor network simulation with cooja,” pp. 641–648, 2006.
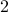 and
and 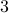 ). With probability
). With probability  the intruders behave as jammers,
while with the remaining probability they behave as legitimate nodes.
the intruders behave as jammers,
while with the remaining probability they behave as legitimate nodes.